 ◎ Server OS: Windows Server 2019
◎ Server OS: Windows Server 2019
◎ OpenVPN: OpenVPN 2.4.9 (Community)
◎ AD verification component: Auth4OpenVPNv2.0
OS Client OS: Windows 10
Due to the company's VPN hardware equipment is old,Recent survey VPN solutions,I want to start with open source solutions first,At the beginning, I thought of OpenVPN, which was tested five years ago.,But after downloading the VM image file from the official website and completing the build,I discovered that this version only opens two free client connections,Subscribe for more。I thought I started charging,No wonder Server and client (OpenVPN Connect) Software interface has become so beautiful,I used to remember to change the settings through the notepad。
Then I found SoftEther VPN from Japan,After spending some time researching and building,I thought this set should work,Unexpectedly, when I was doing the test,,Found a drop SQL connection bug in SoftEther VPN,And netizens have reported the issue for two years,The official still has not corrected,So I had to reluctantly give up。 How to set up SoftEther VPN,Refer to【Notes】SoftEther VPN Server settings。
Later, I looked back for OpenVPN related authorization information,Only found the version of Community,After installing the download,The familiar text file setting screen appears again,Ha。Below is the goal and setting method for this build:
【aims】
◎ Server uses Windows system。
◎ Use AD as the account verification method。
◎ Client side uses independent network segment,And get IP automatically。
◎ Client side will only flow VPN for specific network segment traffic,Go online (Internet) will not。
◎ Client can connect to other network segments within the enterprise。
◎ First,To OpenVPN Community Downloads Download the latest version from the page。
◎ Then refer to the community Easy_Windows_Guide,Complete Server and Client settings,The following capture key settings。
[Preliminary work]
◎ Please tick by yourself when installing “EasyRSA 2 Certificate Management Scripts” element。
◎ Run cmd as "system administrator",And execute the following commands in order:
cd "C:\Program Files\OpenVPN\easy-rsa" init-config notepad vars.bat
◎ Modify the default certificate information,Archive after modification。
set KEY_COUNTRY=US
set KEY_PROVINCE=CA
set KEY_CITY=SanFrancisco
set KEY_ORG=OpenVPN
set KEY_EMAIL=mail@host.domain
◎ Execute the following commands in order:
vars clean-all
【Build Certificate and Key】
◎ Execute the following commands:
build-ca
◎ Enter certificate information:
Country Name (2 letter code) [US]:
State or Province Name (full name) [CA]:
Locality Name (eg, city) [SanFrancisco]:
Organization Name (eg, company) [OpenVPN]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server’s hostname) []:
Email Address [mail@host.domain]:
◎ Execute the following commands in order:
build-key-server server build-key client # Guide 上是建議用 client 端的電腦名稱,然後為每一台電腦產生一份憑證, # 但因為我主要是要用 AD 驗證,所以我這邊是只產生一份名為 client 的憑證,然後讓所有電腦一起使用。 build-dh "C:\Program Files\OpenVPN\bin\openvpn.exe" --genkey --secret "C:\Program Files\OpenVPN\easy-rsa\keys\ta.key"
[Set Server config file]
◎ Execute the following commands:
copy "C:\Program Files\OpenVPN\sample-config\server.ovpn" "C:\Program Files\OpenVPN\easy-rsa\keys\server.ovpn" notepad "C:\Program Files\OpenVPN\easy-rsa\keys\server.ovpn"
◎ Find the following text。
ca ca.crt
cert server.crt
key server.key
dh dh2048.pem
◎ Replace with:
that “C:\\Program Files\OpenVPN\config\ca.crt”
cert “C:\\Program Files\OpenVPN\config\server.crt”
key “C:\\Program Files\OpenVPN\config\server.key”
ie “C:\\Program Files\OpenVPN\config\dh2048.pem”
◎ Archive and close。
◎ Find the following text,And remove the semicolon in front of the comment(;)。Since I plan to make only one voucher for everyone to share,This may cause different clients to obtain the same set of IP,So turn this setting on,So that everyone can get a different IP。
;duplicate-cn
【Set Client config file】
◎ Execute the following commands:
copy "C:\Program Files\OpenVPN\sample-config\client.ovpn" "C:\Program Files\OpenVPN\easy-rsa\keys\client.ovpn" notepad "C:\Program Files\OpenVPN\easy-rsa\keys\client.ovpn"
◎ Find the following text。
ca ca.crt
cert server.crt
key server.key
tls-auth ta.key 1
◎ Replace with:
that “C:\\Program Files\OpenVPN\config\ca.crt”
cert “C:\\Program Files\OpenVPN\config\client.crt”
key “C:\\Program Files\OpenVPN\config\client.key”
tls-auth “C:\\Program Files\OpenVPN\config\ta.key” 1
# Guide does not have this section,This is a mistake when I run the client,And amended。
◎The following “my-server-1” Modify it to the actual FQDN or IP address of OpenVPN。
remote my-server-1 1194
◎ Archive and close。
【Copy certificate、Key to the correct directory]
◎ Execute the following commands:
robocopy "C:\Program Files\OpenVPN\easy-rsa\keys\" "C:\Program Files\OpenVPN\config\" ca.crt ta.key dh2048.pem server.crt server.key server.ovpn
◎ in “C:\Program FilesOpenVPNeasy-rsakeys”,Copy the following files:
ca.crt
ta.key
client.crt
client.key
client.ovpn
◎ posted to the client computer “C:\Program FilesOpenVPNconfig”
PS. The client installation file is the same as Server。
[Start OpenVPN]
◎ Execute OpenVPN GUI as "system administrator" on Server。If you don’t run as "system administrator", you can,But some logs may not have write permission。You can also go to "Windows Service",Masaru “OpenVPNService” Change the "Activation Type" to”automatic”,And right click "activate"。
◎ Client side directly execute OpenVPN GUI,And right-click the icon in the lower right corner and select "Connect"。Client can also be installed with a better interface, OpenVPN Connect,And set the profile (client.opvn) Drag into the window。
The above is the main teaching content of Easy_Windows_Guide,After completing the above settings,You can complete the connection by certificate,Next is to adjust the settings to the environment I want:
◎ Client can connect to other network segments within the enterprise。
◎ Use AD as the account verification method。
[Allow the Client to connect to other network segments within the enterprise]
After OpenVPN is built,The default Server will generate a virtual network card,Its IP is 10.8.0.1,And Client will get 10.8.0.6,At this time Client goes to ping 10.8.0.1 Should pass。
Next, we need to ping the server’s physical network card (Case 192.168.53.1) Will find out,In addition to adding routing at this time,AlsoTurn on the "Internet Connection Sharing" function。I'm stuck here for a long time,Later, it was finally in ViRb3 netizens’ "Create an OpenVPN Windows server that proxies internet traffic · GitHub"This article finds the key setting "Internet Connection Sharing"。
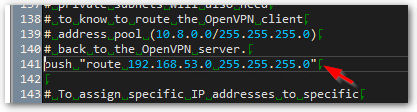
◎ Find the ";push route “192.168…」
◎ According to its format,Add the following,And archive。
push "route 192.168.53.0 255.255.255.0" # 如果要讓 Client 連到企業內部的其他網段, # 可以在這邊加入其他網段的資訊。
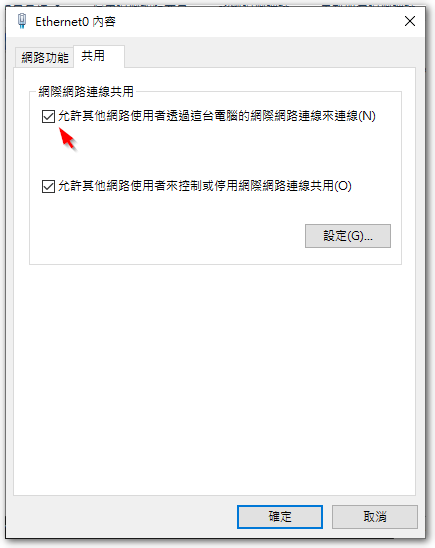
◎ Enter the interface card settings,Turn on the physical network card (192.168.53.1 This one) "Internet Connection Sharing" feature (Tick”Allow other network users to connect through this computer’s Internet connection”)。
PS. I found a lot of articles before I knew how to do this action,Stuck here for a long time。
After turning on the "Internet Connection Sharing" function,The IP of the OpenVPN virtual network card will be changed to 192.168.137.1,So if we want to use OpenVPN’s default 10.8.0.1,Need to modify the machine code。
◎ Run regedit,To the following path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters
◎ Change the value of ScopeAddress to 10.8.0.1。
◎ Restart OpenVPN Server,And let Client reconnect。
[Use AD as the account verification method]
First,Thank you J. Ortega. Written by VBScript,Let's make it easy for OpenVPN to pass AD for verification,Thanks thanks again thanks。In "Active Directory Authentication for OpenVPN For Windows Implementations – amigo4life2"This page has very detailed configuration instructions,But because of the age,So follow up on Windows 2008、2012 Future version,There are still some actions to do,The following is the setting method after finishing:
◎ Download Auth4OpenVPNv2.0.zip,And unzip the content to “C:/Program Files/OpenVPN/Config”
◎ Modify Auth4OpenVPN.ini,Enter information about AD,Examples are as follows:
Server = "192.168.53.20" Domain = "abc" DN = "dc=abc,dc=com,dc=tw" Group = "(Group)OpenVPN" Logging = "On"
Next action,With J. Ortega. Slightly different on the page,This is iceh OpenVPN Community Forum Corrections for security issues in the new version of Windows Server,Thank you iceh netizens。
◎ Open Notepad,Paste the following:
set LOCALAPPDATA=C:\Users\%USERNAME%\AppData\Local set CommonProgramFiles=C:\Program Files\Common Files set CommonProgramFiles(x86)=C:\Program Files (x86)\Common Files set CommonProgramW6432=C:\Program Files\Common Files C:\Windows\System32\cscript.exe "C:\Program Files\OpenVPN\config\Auth4OpenVPN.vbs" exit %errorlevel%
◎Save the file to “C:\Program FilesOpenVPNconfig”,File named “Auth4OpenVPN-64bitWrapper.cmd”。
◎ Add the following two lines of instructions to server.ovpn:
script-security 3 auth-user-pass-verify Auth4OpenVPN-64bitWrapper.cmd via-env
◎ Add the following two lines of instructions to client.ovpn on the Client side:
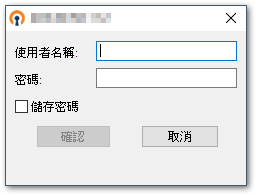
auth-user-pass auth-retry interact
◎ So,Client is connecting,The account password window will pop up to log in。
【Supplementary Information】
◎ Auth4OpenVPN provides test functions,It is recommended to use the following command to test the connection to AD and there is no problem,Let's do follow-up actions。
auth4openvpn.vbs <user> <password>
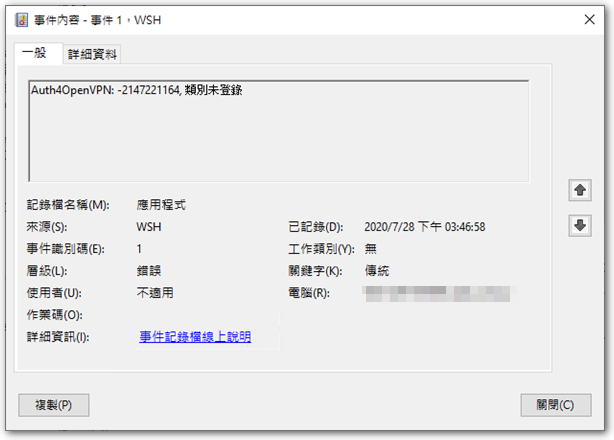
◎ Auth4OpenVPN will leave the verification result in the Windows application log,If set according to the original webpage method,may appear “Auth4OpenVPN: -2147221164, Category not registered” Error message,At this time, according to iceh netizens provided “Auth4OpenVPN-64bitWrapper.cmd” Repair method,Can solve the problem of environmental parameters。
◎ If you want the client to be able to access the Internet through the corporate network (Internet),Just find the following string in the server.ovpn file,And add the previous note(;)Just take it off。
;push "redirect-gateway def1 bypass-dhcp"
◎ OpenVPN Connect when importing the client.ovpn file,Will check if the certificate and key files are in the same directory as the client.ovpn file,If there is no error。After completing the import,When connecting later,OpenVPN Connect will follow the settings of client.ovpn to read the certificate and key files in the command path;OpenVPN GUI does not have this problem。
◎ If you want to verify OpenVPN and Windows native account,You can refer to the shared by smiley22 SAMAuth4OpenVPN element。
◎ Later, I still did not adopt this solution,Because the mainland has filtering for OpenVPN,So there will be some strange problems during the connection process。
【參考連結】
- Community Downloads | OpenVPN
- Easy_Windows_Guide – OpenVPN Community
- Active Directory Authentication for OpenVPN For Windows Implementations – amigo4life2
- (Semi-)Fix for Auth4OpenVPN – Win2008R2 / Win2012R2 – OpenVPN Support Forum
- Create an OpenVPN Windows server that proxies internet traffic · GitHub
- OpenVPN authentication isssue – OpenVPN Support Forum
- OpenVPN Server on Windows ~ Defron.org: Technology, Security, Privacy
- Dead Fox's Pamphlet: Detailed-routing in OpenVPN
- Release SAMAuth4OpenVPN v1.0.0.2 · smiley22/SAMAuth4OpenVPN · GitHub
- [Teaching] OPEN VPN for Windows environment settings @ Fresh afternoon tea :: Tycoon ::
















[…] ◎ Modify Auth4OpenVPN.ini,Enter AD related information,Examples are as follows:? […]
您好,If even 10.8.0.1 fails to ping,It is quite possible that the VPN connection failed to establish,By default,10.8.0.1Can be pinged。
Maybe you can refer to the steps in my article,Set it up step by step,Good luck,Xie Xie
Hello. Thank you for your tutorial, but I have to admit. Let me explain :
I can create a server file on my Windows ( server essentials 2016) and I connect to it from Windows 10 with my client file. The connection is made.
But at the ping stage, when I ping the address 10.8.0.1 from my client station, negative result.
otherwise, as soon as I can connect my client and my server, I no longer have an internet connection on my client workstation.
Do you have a lead to help me get out of this…..
Can the fact that this is an essentials version prevent pinging ?