參加完 2025 資安大會後,感覺透過限制 IP 來源的防護政策還是有一定的效果,因此就在評估對現有 FortiGate VPN 增加相關設定。首先已確認 FortiGate 可以設定以 國家/ 地理位址 做為辨識的「位址物件」,所以後續就剩相關政策的設定與套用。
參加完 2025 資安大會後,感覺透過限制 IP 來源的防護政策還是有一定的效果,因此就在評估對現有 FortiGate VPN 增加相關設定。首先已確認 FortiGate 可以設定以 國家/ 地理位址 做為辨識的「位址物件」,所以後續就剩相關政策的設定與套用。
原先 AI 建議可以在《防火牆政策》設定 Wan → IPSec 來過濾,但實際測試並沒有擋下來,猜測是因為當建置 IPSec VPN 後,FortiGate 會在《進入本機流量政策 (Local-In)》加入一個政策,允許任何 IP 透過 IPSec 連入而造成《防火牆政策》無效,因此要阻擋的話,也需要從這個 Local In Policy 下手了。
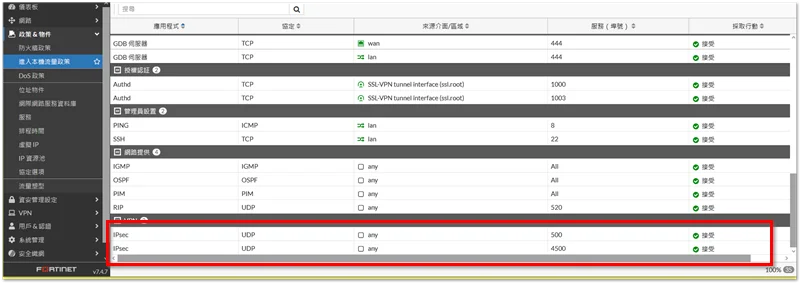
我的韌體版本是 7.4.7,在圖形介面中,Local In Policy 只能檢視,無法異動,因此在建立好相關國家的的「位址物件」後,接下來就需要進入《CLI 控制台》,以指令方式進行 Local In Policy 異動。
(依官方說明,7.6.0 後便可以透過 GUI 設定。)
【FortiGate 環境】
- 韌體版本:7.4.7
- VPN 連線方式:IPSec
- 設定目的:只允許特定國家 IP 可以連線 IPSec VPN。
【CLI 控制台】
先說明一下,以優先順序而言,一般可能會先設定允許的規則,再設定拒絕 All,但因為我想先確認 Deny All 有生效,所以我會先設定 Deny 的規則,等最後全部設完再用 move 去調整 policy 的順序。
1. 拒絕所有 IP 連線 IPSec VPN
config firewall local-in-policy
edit 1
set intf "virtual-wan-link" # virtual-wan-link 為 Interface 的名稱
set srcaddr "all"
set dstaddr "all"
set action deny
set service "IKE" "ESP"
set schedule "always"
next
end
2. 允許特定國家 IP 連線 IPSec VPN
config firewall local-in-policy
edit 2
set intf "virtual-wan-link"
set srcaddr "Country-Allow"
set dstaddr "all"
set action accept
set service "IKE" "ESP"
set schedule "always"
next
end
3. 調整 local-in-policy 順序
config firewall local-in-policy move 2 before 1 end
4. Check the final configuration result
show firewall local-in-policy
[Extras]
在測試的過程,如果有想觀察相關流量狀況,可以透過以下指令進行。
1. 用 sniffer 觀察任何進入 500, 4500 port 的流量
diag sniffer packet any 'port 500 or port 4500' 4 # 4 最詳細,1 最簡單 // 按 CTRL + C 結束
2. 用 debug 模式觀察來自 123.123.123.123 的前 100 筆流量
diag debug reset diag debug flow filter addr 123.123.123.123 diag debug flow trace start 100 diag debug enable diag debug disable diag debug reset
3. 用 debug 模式觀察 IKE 流量
diag debug reset diag debug console timestamp enable diag debug application ike -1 # 等級從 1 ~ 15,-1 代表最詳細 diag debug enable diag debug disable diag debug reset
<Related Links>
- Introduction and Configuration of FortiGate Local-in Policy – Andy’s IT Tech Sharing Website
- How to Change the Order of Local-in Policy… – Fortinet Community